CCP Slave Blocks
C
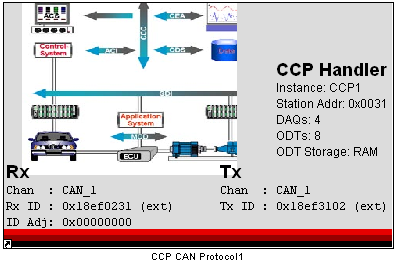
MotoHawk:Blocks:CCP CAN Protocol Handler
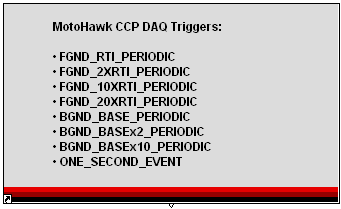
Use this MotoHawk™ block to manage handling of a CAN Calibration Protocol (CCP) connection via CAN. CCP (CAN Calibration Protocol) is a standard intended to create a common interface to electronic control modules. It is possible to use multiple instances of this block, giving each a unique Instance Name, and thus implement multiple CCP handlers. For more information on CCP, see CAN Calibration Protocol. The list of data acquisition (DAQ) triggers is pre-selected to:
- FGND_RTI_PERIODIC
- FGND_2XRTI_PERIODIC
- FGND_10XRTI_PERIODIC
- FGND_20XRTI_PERIODIC
- BGND_BASE_PERIODIC
- BGND_BASEx2_PERIODIC
- BGND_BASEx10_PERIODIC
- ONE_SECOND_EVENT
The CCP Command packets are responded to in IDLE time of the application. To implement a different triggering scheme, use the CCP CAN Protocol External Trigger block from the CCP Slave Library, and supply triggering to the Command Trigger input with a MotoHawk Trigger block.
Supported operations: upload calibrations, download calibrations, data acquisition, seed and key security. Not supported: Flashing operations
MotoHawk:Blocks:CCP MotoHawk Compatibility
There was an issue with the CCP block set, which was fixed with MotoHawk 2010a and later versions.
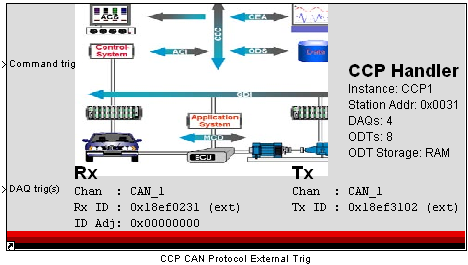
MotoHawk:Blocks:CCP CAN Protocol Handler Trigger
Use this MotoHawk™ block to enable handling a CAN Calibration Protocol (CCP) connection via CAN, with trigger inputs for Command Objects and Data Acquisitions. Note: Do not place this block at the top level of a model, but at a subsequent lower level, if the Matlab version in use is 2007a or later, as this can cause triggering complications.
Command trig: Connect a MotoHawk Trigger (or triggering from the CCP Triggers block) to the input to determine when CCP commands will be processed.
DAQ trig(s): Connect a vector of MotoHawk Trigger blocks to the input. These triggers determine the possible data acquisition rates (unique DAQ list rates).
Response to CCP Command packets is completed in the CAN interrupt in which they occur. For more information on CCP, see CAN Calibration Protocol.
Supported operations: upload calibrations, download calibrations, data acquisition, seed and key security.
Not supported: Flashing operations
MotoHawk:Blocks:CCP Security Challenge Seed & Key (CAL)
Use this MotoHawk™ block to set a Seed & Key value when security authentication is required for CCP access.
This block should be used in conjunction with a Security Challenge Request Trigger to provide 32-bit Seed and Key values to be used in GET_SEED and UNLOCK CCP commands. Instance Name must match the instance name assigned in the CCP Handler block.
Supply the "seed" value to the upper left input on the block, the "key" value to the bottom left input, and the response complete trigger signal to the top input.
Note: There are CAL-designated blocks and DAQ-designated blocks. The respectively named CAL and DAQ blocks are functional equivalents and are actually interchangeable; these block names serve to inform that it may be useful to have security access requirements for calibration activity as separate and distinct from the security for data acquisition requests. For instance, one would typically use the (CAL) set to configure a security scheme for a calibration request, and/or set up security for a data acquisition request using the (DAQ) blocks.
MotoHawk:Blocks:CCP Security Challenge Seed & Key (DAQ)
Use this MotoHawk™ block to set a Seed & Key value when security authentication is required for CCP access.
Use this block should be used in conjunction with a Security Challenge Request Trigger to provide 32-bit Seed and Key values to be used in GET_SEED and UNLOCK CCP commands. Instance Name must match the instance name assigned in the CCP Handler block.
Supply the "seed" value to the upper left input on the block, the "key" value to the bottom left input, and the response complete trigger signal to the top input.
Note: There are CAL-designated blocks and DAQ-designated blocks. The respectively named CAL and DAQ blocks are functional equivalents and are actually interchangeable; these block names serve to inform that it may be useful to have security access requirements for calibration activity as separate and distinct from the security for data acquisition requests. For instance, one would typically use the (CAL) set to configure a security scheme for a calibration request, and/or set up security for a data acquisition request using the (DAQ) blocks.
MotoHawk:Blocks:CCP Security Challenge Trigger (CAL)
Use this MotoHawk™ block to fire a trigger if a GET_SEED CCP command is issued by the client.
Connected to this trigger should be a security function and a Security Challenge Seed & Key block to provide 32-bit Seed & Key values for the request. The security function can be any function where the Key can be computed from the Seed via a "known" function. The client must have the identical function to be able to compute the key. For improved security, the Seed value should be as random as possible. Consider using the absolute time block along with the module serial number to create a pseudo-random seed. Instance Name must match the instance name assigned in the CCP Handler block.
Note: There are CAL-designated blocks and DAQ-designated blocks. The respectively named CAL and DAQ blocks are functional equivalents and are actually interchangeable; these block names serve to inform that it may be useful to have security access requirements for calibration activity as separate and distinct from the security for data acquisition requests. For instance, one would typically use the (CAL) set to configure a security scheme for a calibration request, and/or set up security for a data acquisition request using the (DAQ) blocks.
MotoHawk:Blocks:CCP Security Challenge Trigger (DAQ)
Use this MotoHawk™ block to fire a trigger if a GET_SEED CCP command is issued by the client.
Connected to this trigger should be a security function and a Security Challenge Seed & Key block to provide the 32-bit Seed & Key values for the request. The security function can be any function where the Key can be computed from the Seed via a "known" function. The client must have the identical function to be able to compute the key. For improved security, the Seed value should be as random as possible. Consider using the absolute time block along with the module serial number to create a pseudo-random seed. Instance Name must match the instance name assigned in the CCP Handler block.
Note: There are CAL-designated blocks and DAQ-designated blocks. The respectively named CAL and DAQ blocks are functional equivalents and are actually interchangeable; these block names serve to inform that it may be useful to have security access requirements for calibration activity as separate and distinct from the security for data acquisition requests. For instance, one would typically use the (CAL) set to configure a security scheme for a calibration request, and/or set up security for a data acquisition request using the (DAQ) blocks.
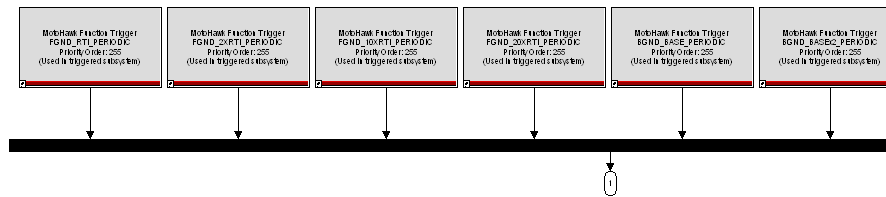
MotoHawk:Blocks:CCP CAN DAQ Triggers
Use this MotoHawk™ block to provide one or several data acquisition (DAQ) triggers for use in handling a CAN Calibration Protocol (CCP) connection via CAN.
Double-click on this block to open; the default function trigger scheme opens. These triggers are tied to a multiplexer, which is typically fed to the Command Trigger input of the CCP CAN Protocol Handler External Trigger block. To change the triggering attributes or scheme, open this block and then delete, add or edit trigger blocks as needed.